Technology
How to Be Invisible on the Internet
Everywhere you look, concerns are mounting about internet privacy.
Although giving up your data was once an afterthought when gaining access to the newest internet services such as Facebook and Uber, many people have had their perspective altered by various recent scandals, billions of dollars of cybertheft, and a growing discomfort around how their personal data may be used in the future.
More people want to opt out of this data collection, but aside from disconnecting entirely or taking ludicrous measures to safeguard information, there aren’t many great options available to limit what is seen and known about you online.
The Next Best Thing
It may not be realistic to use Tor for all online browsing, so why not instead look at taking more practical steps to reducing your internet footprint?
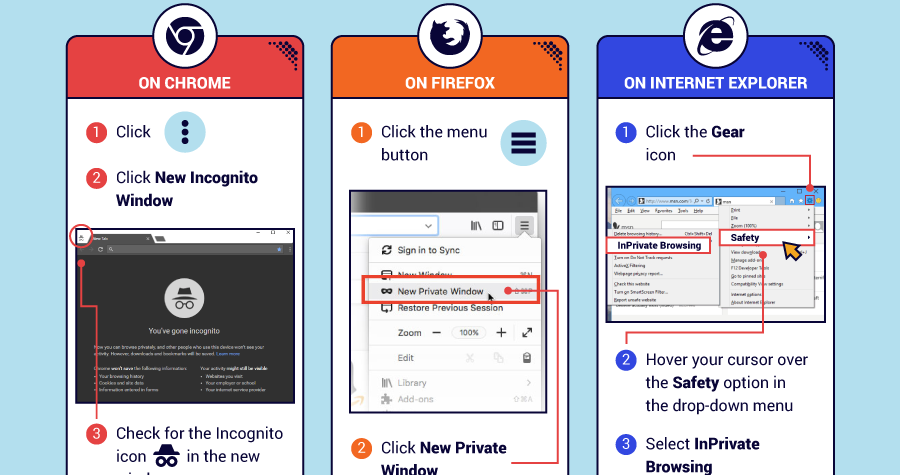
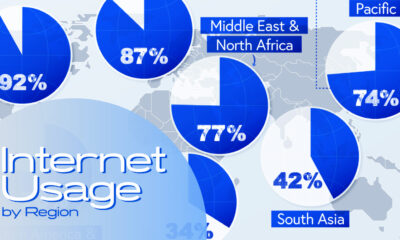
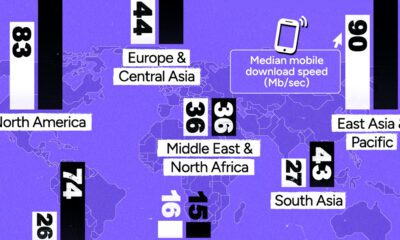
Today’s infographic comes to us from CashNetUSA, and it gives a step-by-step guide – that anyone can follow – to limit the amount of personal data that gets collected on the internet.
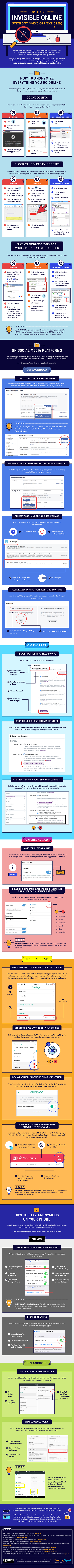
As you can see, you can take simple steps to limit the amount of personal information you give up online.
To be absolutely clear, these actions will not reduce your footprint to nothing – but they will make many important categories of data invisible for all intents and purposes.
Basic Building Blocks
The simple actions that can be taken fall into three major realms: internet browsers, social networks, and mobile phones.
1. Internet Browsers:
Whether you are using Chrome, Firefox, or Internet Explorer, there are easy things you can do to increase privacy. These include using private browsing, blocking third-party cookies, and tailoring the permissions for websites that you access.
2. Social Media Platforms
Major social networks have options built-in for users seeking privacy – it’s just many people don’t know they are there. On Facebook, for example, you can prevent your name being linked to ads – and on Twitter, you can prevent Twitter from tracking you.
3. Mobile Phones
We live more and more on our smartphones, but thankfully there are options here as well. You can block ad tracking on Safari, or opt out of ad personalization on Android. There is even a simple setting on Android that allows you to encrypt your phone.
Technology
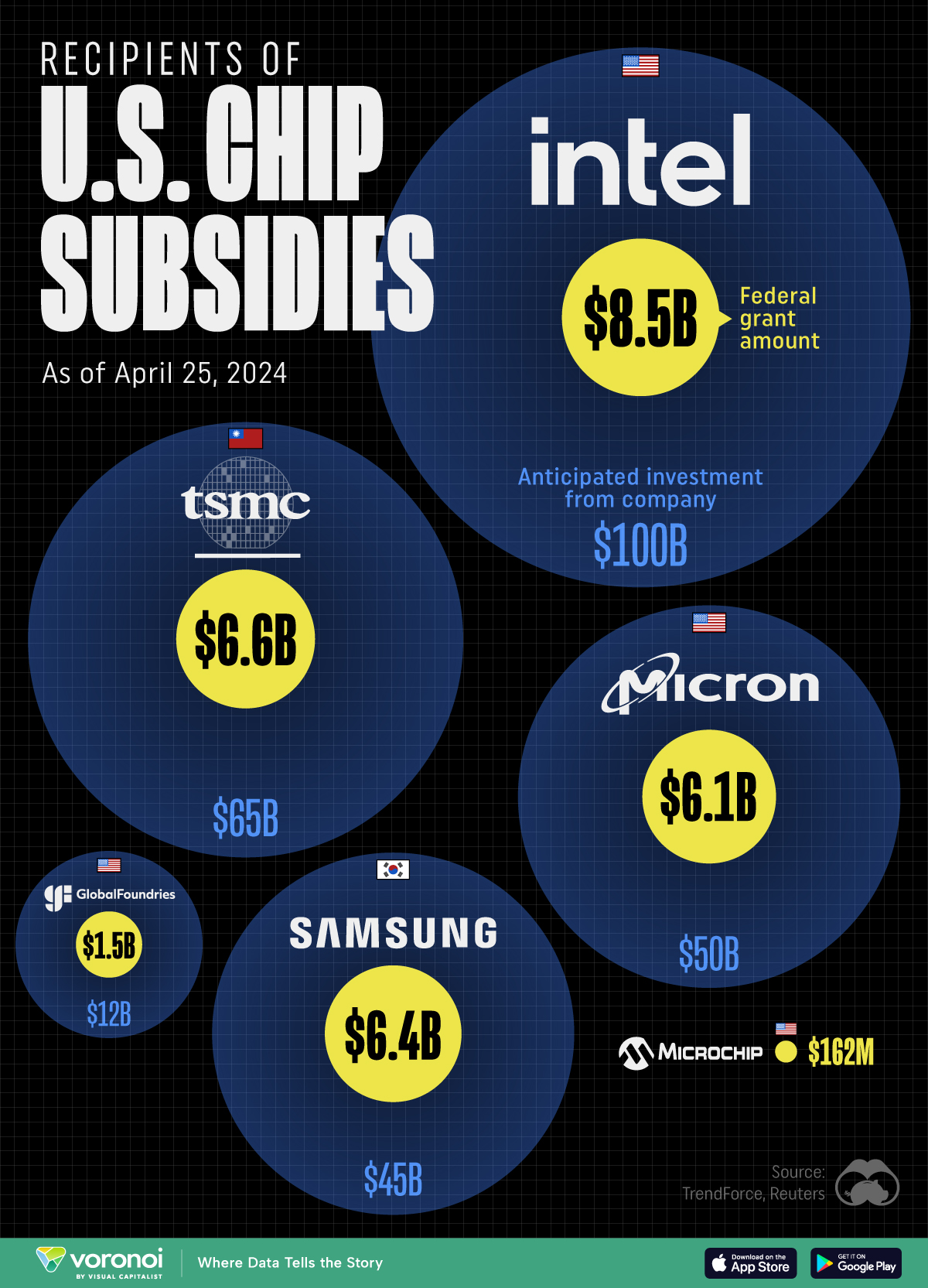
All of the Grants Given by the U.S. CHIPS Act
Intel, TSMC, and more have received billions in subsidies from the U.S. CHIPS Act in 2024.

All of the Grants Given by the U.S. CHIPS Act
This was originally posted on our Voronoi app. Download the app for free on iOS or Android and discover incredible data-driven charts from a variety of trusted sources.
This visualization shows which companies are receiving grants from the U.S. CHIPS Act, as of April 25, 2024. The CHIPS Act is a federal statute signed into law by President Joe Biden that authorizes $280 billion in new funding to boost domestic research and manufacturing of semiconductors.
The grant amounts visualized in this graphic are intended to accelerate the production of semiconductor fabrication plants (fabs) across the United States.
Data and Company Highlights
The figures we used to create this graphic were collected from a variety of public news sources. The Semiconductor Industry Association (SIA) also maintains a tracker for CHIPS Act recipients, though at the time of writing it does not have the latest details for Micron.
| Company | Federal Grant Amount | Anticipated Investment From Company |
|---|---|---|
| 🇺🇸 Intel | $8,500,000,000 | $100,000,000,000 |
| 🇹🇼 TSMC | $6,600,000,000 | $65,000,000,000 |
| 🇰🇷 Samsung | $6,400,000,000 | $45,000,000,000 |
| 🇺🇸 Micron | $6,100,000,000 | $50,000,000,000 |
| 🇺🇸 GlobalFoundries | $1,500,000,000 | $12,000,000,000 |
| 🇺🇸 Microchip | $162,000,000 | N/A |
| 🇬🇧 BAE Systems | $35,000,000 | N/A |
BAE Systems was not included in the graphic due to size limitations
Intel’s Massive Plans
Intel is receiving the largest share of the pie, with $8.5 billion in grants (plus an additional $11 billion in government loans). This grant accounts for 22% of the CHIPS Act’s total subsidies for chip production.
From Intel’s side, the company is expected to invest $100 billion to construct new fabs in Arizona and Ohio, while modernizing and/or expanding existing fabs in Oregon and New Mexico. Intel could also claim another $25 billion in credits through the U.S. Treasury Department’s Investment Tax Credit.
TSMC Expands its U.S. Presence
TSMC, the world’s largest semiconductor foundry company, is receiving a hefty $6.6 billion to construct a new chip plant with three fabs in Arizona. The Taiwanese chipmaker is expected to invest $65 billion into the project.
The plant’s first fab will be up and running in the first half of 2025, leveraging 4 nm (nanometer) technology. According to TrendForce, the other fabs will produce chips on more advanced 3 nm and 2 nm processes.
The Latest Grant Goes to Micron
Micron, the only U.S.-based manufacturer of memory chips, is set to receive $6.1 billion in grants to support its plans of investing $50 billion through 2030. This investment will be used to construct new fabs in Idaho and New York.
-
 Debt1 week ago
Debt1 week agoHow Debt-to-GDP Ratios Have Changed Since 2000
-
 Markets2 weeks ago
Markets2 weeks agoRanked: The World’s Top Flight Routes, by Revenue
-

 Countries2 weeks ago
Countries2 weeks agoPopulation Projections: The World’s 6 Largest Countries in 2075
-
 Markets2 weeks ago
Markets2 weeks agoThe Top 10 States by Real GDP Growth in 2023
-
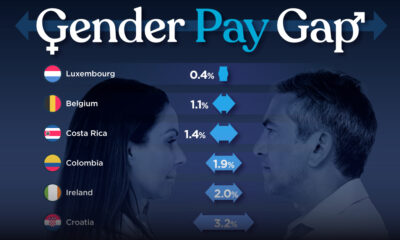
 Demographics2 weeks ago
Demographics2 weeks agoThe Smallest Gender Wage Gaps in OECD Countries
-
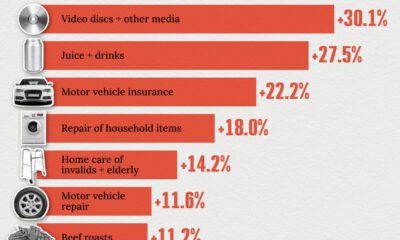
 United States2 weeks ago
United States2 weeks agoWhere U.S. Inflation Hit the Hardest in March 2024
-

 Green2 weeks ago
Green2 weeks agoTop Countries By Forest Growth Since 2001
-
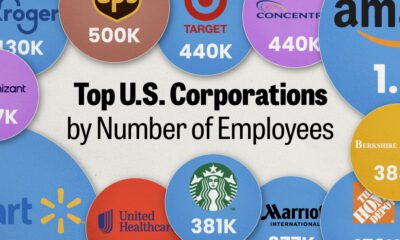
 United States2 weeks ago
United States2 weeks agoRanked: The Largest U.S. Corporations by Number of Employees