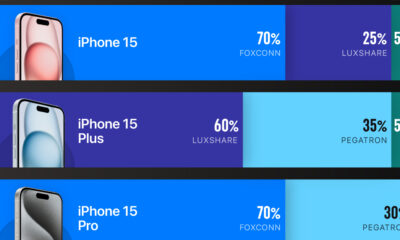
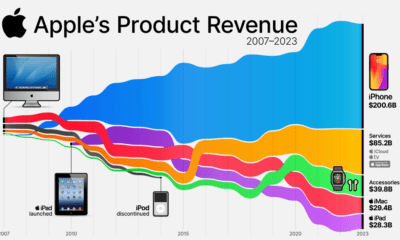
Technology
The Cybersecurity Boom

The Cybersecurity Boom
How Investors Can Play the Global Explosion in Cyberattacks and Cybercrime
Thanks to Purefunds Cybersecurity ETF (HACK) for helping us put this together.
In 1983’s WarGames, a young Matthew Broderick unwittingly hacks into military central computer while searching for video games and almost inadvertently starts World War III. This film is classified on IMDB as in the “Sci-fi, Thriller” genres.
While the prospects of cybercrime and cyberterrorism are certainly thrilling (and scary), the descriptor of “Sci-fi” for the movie may no longer be necessary. In the last calendar year, there’s been dozens of high-profile cybersecurity incidents that are not a far cry from the geopolitical near-miss in WarGames.
The United States government and the country’s largest bank have both had serious security intrusions as of recent. This summer the United States Government revealed it had over 20 million records stolen by hackers allegedly based in China. Just as concerning, it was exactly one year ago that J.P. Morgan was compromised with records stolen from over 76 million households and 7 million small businesses. The company has now vowed to spend $250 million a year in preventing such incidents.
Most recent of all is this week’s hack of the popular adultery site Ashley Madison. The leak of sensitive information on potentially 37 million customers isn’t a potential geopolitical concern as the above cases, but it does have business implications: the website’s plan to raise $200 million in an IPO in London has now been kiboshed for the foreseeable future.
If big organizations like Sony, Target, Google, and Home Depot can’t do anything to stop cybersecurity incidents, what chance do the rest of us have?
And that’s the problem with cyberattacks. Detected incidents have skyrocketed over the last five years, soaring from 3.4 million to 42.8 million from 2009-2014, and they now cost the global economy an estimated $400 billion a year. Every day these incidents happen on a small scale, but today’s hacking technology and sophistication allows for much more. Exploitation of big cybersecurity vulnerabilities could cause financial chaos, destroy reputations of entire companies, expose business and state secrets, and even shut down moving vehicles remotely. This is not science fiction. This is reality – and we haven’t even gotten into the hypothetical potential damage that hackers could cause if they had even more resources or resolve. People’s lives and money are at stake.
Systems are more sensitive and hyperconnected than ever before, and hackers are deploying more sophisticated tactics to take advantage of them for personal or organizational gain. Luckily, there is also an entire industry of engineers, programmers, analysts, designers, cryptographers, and other professionals trying to build the walls and moat around the castle. Cybersecurity, as we depict in this infographic, is a booming industry with hundreds of companies scrambling to protect us from having intellectual property, health records, financial information, and other vital data compromised.
That’s why by 2020, the cybersecurity market is expected to be valued at $170.2 billion, which implies a 9.8% CAGR (compound annual growth rate) from today’s estimate of $106.3 billion. Businesses and governments are spending more on cybersecurity: even the Whitehouse announced this year that in its 2016 fiscal budget that it would aim to spend $14 billion on additional measures. Fifteen years ago, cybersecurity was only a blip on the US government’s radar at $938 million in spending.
The private sector is in the same boat, as 69% of business executives see cyberattacks as a threat to their growth. This is a fair statement since Verizon estimates in its 2015 Data Breach Investigations Report that the average cost of a cyberattack to a business ranges between $475,000 to $9 million depending on the number of records stolen.
Among the companies that are benefiting from the surge in cybersecurity spending include those building firewalls, secure servers, routers, anti-virus software, and malware detection tools. Firms that specialize in consulting and solving related security problems are also getting plenty of interest. Investors can potentially profit from this sector as well by identifying companies and funds that will gain from booming activity and spending in the sector.
Brands
How Tech Logos Have Evolved Over Time
From complete overhauls to more subtle tweaks, these tech logos have had quite a journey. Featuring: Google, Apple, and more.

How Tech Logos Have Evolved Over Time
This was originally posted on our Voronoi app. Download the app for free on iOS or Android and discover incredible data-driven charts from a variety of trusted sources.
One would be hard-pressed to find a company that has never changed its logo. Granted, some brands—like Rolex, IBM, and Coca-Cola—tend to just have more minimalistic updates. But other companies undergo an entire identity change, thus necessitating a full overhaul.
In this graphic, we visualized the evolution of prominent tech companies’ logos over time. All of these brands ranked highly in a Q1 2024 YouGov study of America’s most famous tech brands. The logo changes are sourced from 1000logos.net.
How Many Times Has Google Changed Its Logo?
Google and Facebook share a 98% fame rating according to YouGov. But while Facebook’s rise was captured in The Social Network (2010), Google’s history tends to be a little less lionized in popular culture.
For example, Google was initially called “Backrub” because it analyzed “back links” to understand how important a website was. Since its founding, Google has undergone eight logo changes, finally settling on its current one in 2015.
| Company | Number of Logo Changes |
|---|---|
| 8 | |
| HP | 8 |
| Amazon | 6 |
| Microsoft | 6 |
| Samsung | 6 |
| Apple | 5* |
Note: *Includes color changes. Source: 1000Logos.net
Another fun origin story is Microsoft, which started off as Traf-O-Data, a traffic counter reading company that generated reports for traffic engineers. By 1975, the company was renamed. But it wasn’t until 2012 that Microsoft put the iconic Windows logo—still the most popular desktop operating system—alongside its name.
And then there’s Samsung, which started as a grocery trading store in 1938. Its pivot to electronics started in the 1970s with black and white television sets. For 55 years, the company kept some form of stars from its first logo, until 1993, when the iconic encircled blue Samsung logo debuted.
Finally, Apple’s first logo in 1976 featured Isaac Newton reading under a tree—moments before an apple fell on his head. Two years later, the iconic bitten apple logo would be designed at Steve Jobs’ behest, and it would take another two decades for it to go monochrome.
-

 Travel1 week ago
Travel1 week agoAirline Incidents: How Do Boeing and Airbus Compare?
-
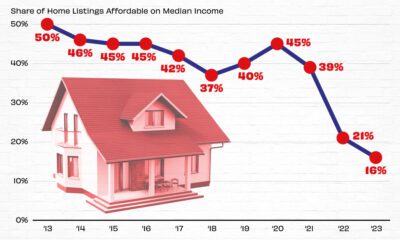
 Markets2 weeks ago
Markets2 weeks agoVisualizing America’s Shortage of Affordable Homes
-

 Green2 weeks ago
Green2 weeks agoRanked: Top Countries by Total Forest Loss Since 2001
-

 Money2 weeks ago
Money2 weeks agoWhere Does One U.S. Tax Dollar Go?
-
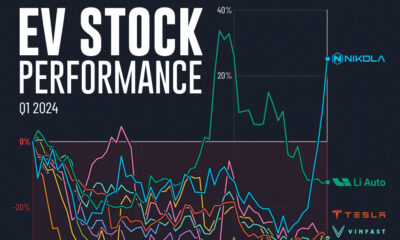
 Misc2 weeks ago
Misc2 weeks agoAlmost Every EV Stock is Down After Q1 2024
-
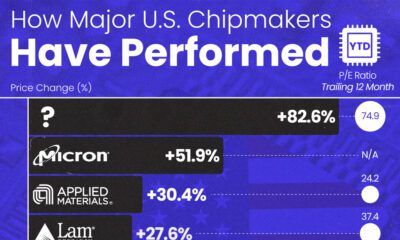
 AI2 weeks ago
AI2 weeks agoThe Stock Performance of U.S. Chipmakers So Far in 2024
-

 Markets2 weeks ago
Markets2 weeks agoCharted: Big Four Market Share by S&P 500 Audits
-

 Real Estate2 weeks ago
Real Estate2 weeks agoRanked: The Most Valuable Housing Markets in America